Mapping a Curriculum to the NICE Cybersecurity Workforce Framework
Here’s a scenario: a cybersecurity analyst might have to respond to a network that has been compromised by sophisticated malware evading traditional...

Senit Lutgen is a student in the Winter 2023 Cohort of our Cyber Defense Analyst Bootcamp. Below, he details some of the tell-tale signs that a phishing attempt is masquerading as a legitimate email. This post was originally published on his LinkedIn page.
***
This is a little gem that we got recently. It was pretty obvious to us that it was not legit.
However when I first saw it, I thought these cyber-crooks had done a pretty good job. Nah! But, why did I think that?
Humans can understand error laden written communications. It may annoy us, but it doesn’t stop us. Add in an emotional distraction that is demanding urgent action, and we have a recipe to get scammed.
So, when I took just a few minutes to actually read this email, I was amazed at how bad and obvious it really was.
🔑 The key is to slow down and focus. Pretty simple right? But not something we like to do in our busy lives.
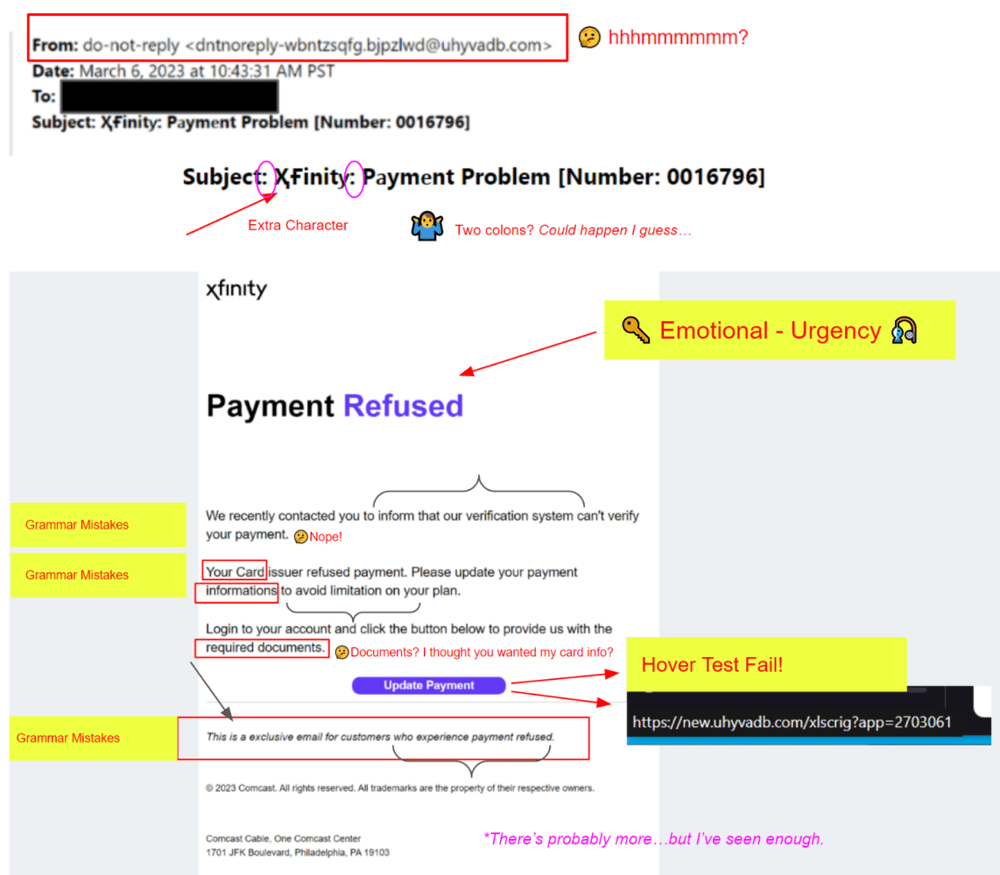
Program a new rule into your brain.
Anytime you get an email that begs or demands urgent action and/or that has an emotional element (anger, surprise, fear…), take a breath and slow down.
Set your mind to the hypothesis that this email is illegitimate and then work toward disproving that. If you cannot disprove that to your satisfaction, then don’t take that hook!
Also, does it really matter if you take 5 to 15 minutes to investigate before acting? Probably not!
Do not click any links or call any numbers. Certainly, never enter or provide any information at this stage (if at all). If you really cannot help yourself from taking action, then do so by using a verified company portal or phone number. Never take action through the email.
Here are some simple things to examine:
Just never take action or click on any of the links in the email. Only take action through trusted sources (phone numbers, emails, and web pages) that you know are legitimate.

Here’s a scenario: a cybersecurity analyst might have to respond to a network that has been compromised by sophisticated malware evading traditional...

Cyber hygiene. It’s a term thrown around quite a bit in the cybersecurity industry, but what is it?

Malware, which is short for malicious software, is any software that is designed to cause damage to computer systems, networks, or devices. Malware...